WLAN: Unterschied zwischen den Versionen
| Zeile 27: | Zeile 27: | ||
'identity="USERNAME"' | 'identity="USERNAME"' | ||
'password="YOUR_PASSWORD"' | 'password="YOUR_PASSWORD"' | ||
| − | 'ca_cert="hash://server/sha256/ | + | 'ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb"' |
'phase2="auth=PAP"' | 'phase2="auth=PAP"' | ||
) | ) | ||
| Zeile 46: | Zeile 46: | ||
password="YOUR_PASSWORD" | password="YOUR_PASSWORD" | ||
phase2="auth=PAP" | phase2="auth=PAP" | ||
| − | ca_cert="hash://server/sha256/ | + | ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb" |
} | } | ||
</syntaxhighlight> | </syntaxhighlight> | ||
| Zeile 102: | Zeile 102: | ||
anonymous_identity="$_ANONYMOUS_IDENTITY" | anonymous_identity="$_ANONYMOUS_IDENTITY" | ||
phase2="auth=PAP" | phase2="auth=PAP" | ||
| − | ca_cert="hash://server/sha256/ | + | ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb" |
} | } | ||
</syntaxhighlight> | </syntaxhighlight> | ||
Version vom 10. April 2017, 21:07 Uhr
We're moving our wifi infrastructure to an authenticated and encrypted ssid. At the moment it's hard to change our internal wifi password, because our door system depends on it. If you are not in our internal wifi you can't operate the door.
This is one reason why we want to use 802.1x with EAP-TTLS. Every member has it's own username/password combination which can be reset or changed through a webinterface. If a member quits the space, we just have to deactivate the account and the internal access is gone.
The other reason is: Every member has its own encrypted channel to our access points. In addition the member has the possibility to check, if the SSID can be trusted (avoid roque APs) with an ssl certificate
certificate
To check if you're connecting to the correct SSID, you can and should add the ssl certificate to your connection setting. You can download the SSL CA-Certificate from our Server.
netctl
Save config as /etc/netctl/$interfacename-backspace_8021x. You have to restart netctl-auto (e.g. systemctl restart netctl-auto@$interface)
Description='backspace WPA2 802.1X'
Interface=wlp3s0
Connection=wireless
Security=wpa-configsection
IP=dhcp
ESSID="backspace 802.1x"
WPAConfigSection=(
'ssid="backspace 802.1x"'
'proto=RSN WPA'
'key_mgmt=WPA-EAP'
'eap=TTLS'
'identity="USERNAME"'
'password="YOUR_PASSWORD"'
'ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb"'
'phase2="auth=PAP"'
)FYI: Replace the interface name according to your system
wpa_supplicant
Add to /etc/wpa_supplicant/wpa_supplicant.conf:
network={
ssid="backspace 802.1x"
key_mgmt=WPA-EAP
eap=TTLS
identity="USERNAME"
password="YOUR_PASSWORD"
phase2="auth=PAP"
ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb"
}connman
UNTESTED!
[service_backspace]
Type=wifi
Name="backspace 802.1x"
EAP=ttls
Phase2=PAP
Identity=USERNAME
Passphrase=YOUR_PASSWORD
CACertFile = /etc/ssl/certs/ca-bundle.crtSailfish OS
Tested and working
Put the following into /var/lib/connman/wifi_bckspc-8021x.config
then
systemctl restart connman
[service_backspace]
Type = wifi
Name = backspace 802.1x
EAP = ttls
Phase2 = PAP
Identity = USERNAME
Passphrase = PASSWORD
CACertFile = /etc/ssl/certs/ca-bundle.crtwicd
ctrl_interface=/var/run/wpa_supplicant
network={
ssid="backspace 802.1x"
scan_ssid=$_SCAN
identity="USERNAME"
password="YOUR_PASSWORD"
proto=WPA2
key_mgmt=WPA-EAP
group=CCMP
pairwise=CCMP
eap=TTLS
anonymous_identity="$_ANONYMOUS_IDENTITY"
phase2="auth=PAP"
ca_cert="hash://server/sha256/d5d218433d7a94b562b58583998035a9526e263e809ac78ca777029c9e3a1bfb"
}Warning: This is not yet tested. ca_cert certificate checking should work as it does for netctl and wpa_supplicant. Adapted from 31c3 wiki
Android
This is how you can connect with the android operating system to our 802.1x WIFI (WPA2 Enterprise)
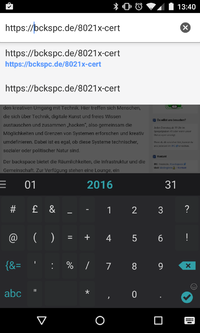
- Download our certificate at https://bckspc.de/8021x-cert
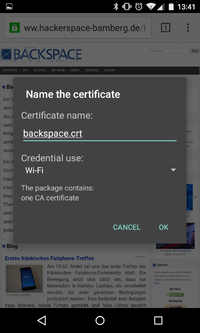
- Open downloaded certificate
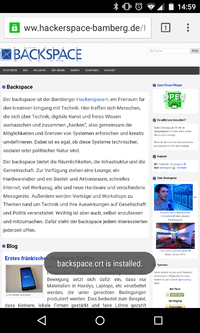
- Save certificate as backspace.crt and type "Wifi"
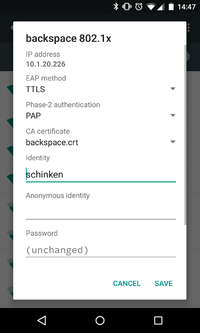
- Modify/Configure your backspace 802.1x connection according to the screenshot below
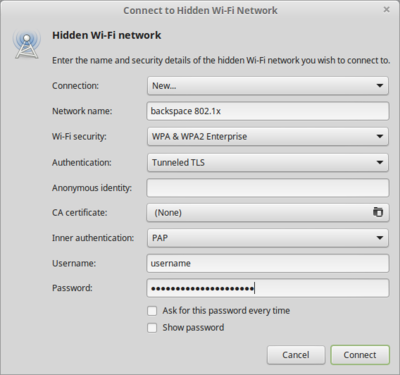
Linux - NetworkManager
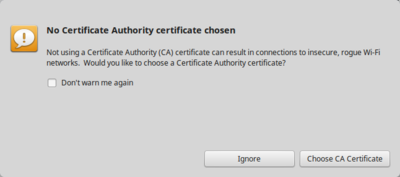
Ignore the certificate warning as long as we don't provide a certificate.
Mac OS X
The following procedure has been tested using Mac OS 10.11 El Capitan.
Earlier versions of OS X offered to specify the authentication protocol when connecting to a wireless network. However, in newer versions you'll have to install a configuration profile in order to connect to our network using 802.1x with EAP-TTLS/PAP. This configuration profile contains our certificate and all required settings.
- Backspace.mobileconfig
MD5: 7ca7ff1eb4f0fda8039dc079430c870e
SHA1: c395a6e090ed21e2c346b5784f2a4ee2d34bf290
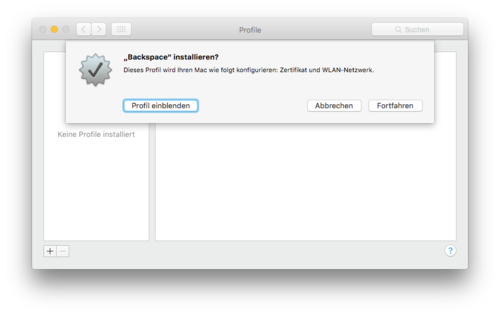
Simply download the file to your computer. You can check its integrity using the provided checksums. After opening the file, confirm the installation.
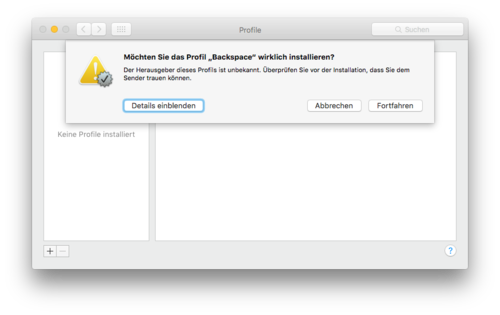
Please note that the configuration profile is not signed. Therefore you'll also have to confirm the following warning.
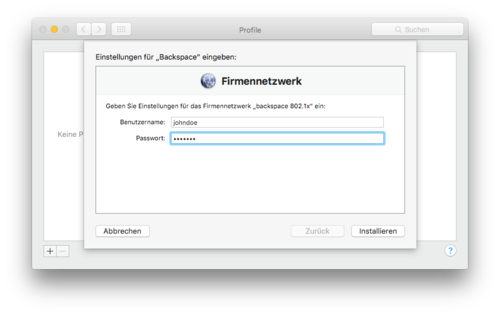
When asked for a username and password, enter your Backspace credentials.
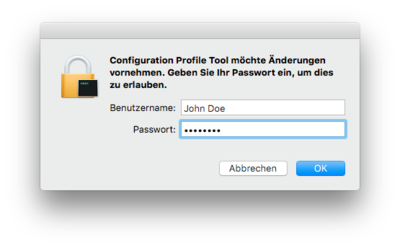
Confirm the installation using your OS X account credentials:
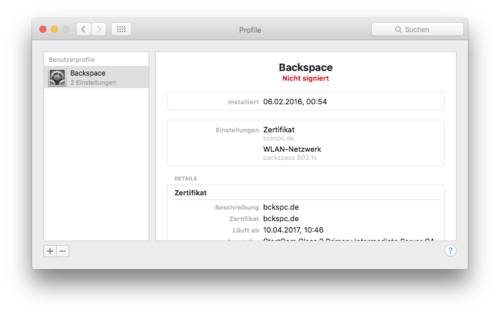
You should now see the 'Backspace' profile in the profiles dialog:
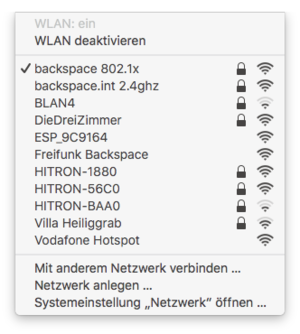
After the profile has been installed, connect to the 'backspace 802.1x' network:
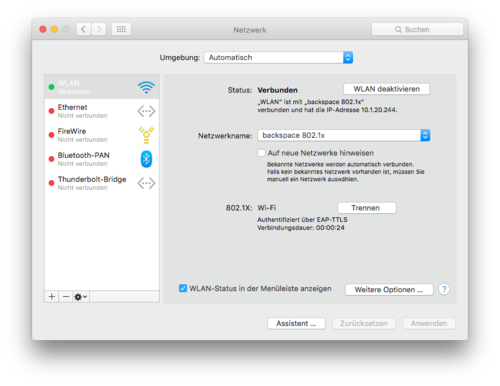
You can verify your connection setup by looking for an IP address in the network configuration dialog. The authentication status next to '802.1X' should read 'Authenticated by EAP-TTLS':
iOS
Download the configuration profile to your iOS device and install it. When asked for a username and password, enter your Backspace credentials. After that, you should be able to connect to the 'backspace 802.1x' network.
Windows 7
Windows 7 does not support EAP-TTLS / PAP from scratch. The same is true for eduroam networks and this is why there are a lot of instructions from universities which use SecureW2 as an additional Software to enable EAP-TTLS:
Unfortunately, SecureW2 is not free (it used to be, but they revoked that).
Another option could be XSupplicant from the Open1X project; they were working towards Windows 7 support, but it seems that they didn't make it. (Latest news is from 25 Sept 2010 that version 2.2.2 should support it; I tried v2.2.2.504.x64, didn't work).
To summarize, right now we do not know a free option to connect with EAP-TTLS / PAP under Windows 7.
(read this article for a good discussion on the tool market and other commercial options)
Windows 8 and above
Since Windows 8 the system itself is capable of EAP-TTLS.
TODO: Someone with windows should do some screenshots.