WLAN: Unterschied zwischen den Versionen
(→netctl) |
|||
| Zeile 2: | Zeile 2: | ||
{{Ambox|text=This is currently in beta phase! We're going to provide a certificate soon!}} | {{Ambox|text=This is currently in beta phase! We're going to provide a certificate soon!}} | ||
| + | We're moving our wifi infrastructure to an authenticated and encrypted ssid. At the moment it's hard to change our internal wifi password, because our door system depends on it. If you are not in our internal wifi you can't operate the door. | ||
| + | |||
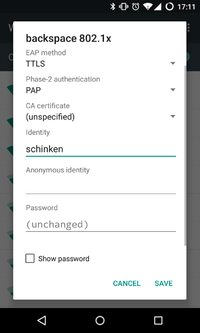
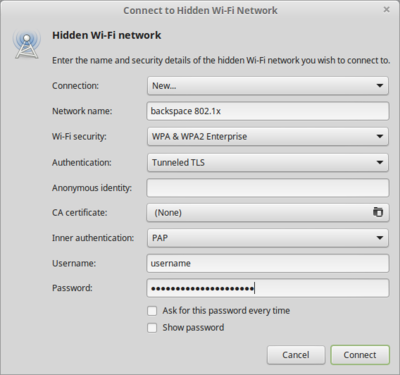
| + | This is one reason why we want to use 802.1x with EAP-TTLS. Every member has it's own username/password combination which can be reset or changed through a webinterface. If a member quits the space, we just have to deactivate the account and the internal access is gone. | ||
| + | |||
| + | The other reason is: Every member has it's own encrypted channel to our access points. In addition the member has the possibility to check, if the SSID can be trusted (avoid roque APs) with an ssl certificate | ||
== netctl == | == netctl == | ||
Version vom 17. Januar 2016, 21:50 Uhr
| This is currently in beta phase! We're going to provide a certificate soon! |
We're moving our wifi infrastructure to an authenticated and encrypted ssid. At the moment it's hard to change our internal wifi password, because our door system depends on it. If you are not in our internal wifi you can't operate the door.
This is one reason why we want to use 802.1x with EAP-TTLS. Every member has it's own username/password combination which can be reset or changed through a webinterface. If a member quits the space, we just have to deactivate the account and the internal access is gone.
The other reason is: Every member has it's own encrypted channel to our access points. In addition the member has the possibility to check, if the SSID can be trusted (avoid roque APs) with an ssl certificate
netctl
Save config as /etc/netctl/$interfacename-backspace_8021x. You have to restart netctl-auto (e.g. systemctl restart netctl-auto@$interface)
Description='backspace WPA2 802.1X'
Interface=wlp3s0
Connection=wireless
Security=wpa-configsection
IP=dhcp
ESSID="backspace 802.1x"
WPAConfigSection=(
'ssid="backspace 802.1x"'
'proto=RSN WPA'
'key_mgmt=WPA-EAP'
'eap=TTLS'
'identity="USERNAME"'
'password="YOUR_PASSWORD"'
'phase2="auth=PAP"'
)wpa_supplicant
Add to /etc/wpa_supplicant/wpa_supplicant.conf:
network={
ssid="backspace 802.1x"
key_mgmt=WPA-EAP
eap=TTLS
identity="USERNAME"
password="YOUR_PASSWORD"
phase2="auth=PAP"
}connman
UNTESTED!
[service_backspace]
Type=wifi
Name="backspace 802.1x"
EAP=ttls
Phase2=PAP
Identity=USERNAME
Passphrase=YOUR_PASSWORDwicd
ctrl_interface=/var/run/wpa_supplicant
network={
ssid="backspace 802.1x"
scan_ssid=$_SCAN
identity="USERNAME"
password="YOUR_PASSWORD"
proto=WPA2
key_mgmt=WPA-EAP
group=CCMP
pairwise=CCMP
eap=TTLS
anonymous_identity="$_ANONYMOUS_IDENTITY"
phase2="auth=PAP"
}Android
Linux - NetworkManager
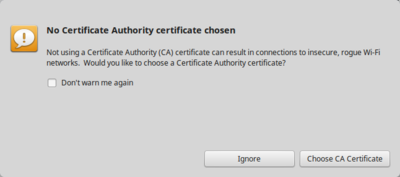
Ignore the certificate warning as long as we don't provide a certificate.